Researchers Detail Critical RCE Flaw Reported in Popular vm2 JavaScript Sandbox

A now-patched security flaw in the vm2 JavaScript sandbox module could be abused by a remote adversary to break out of security barriers and perform arbitrary operations on the underlying machine.
JavaScript sandbox vm2 remediates remote code execution risk
"A threat actor can bypass the sandbox protections to gain remote code execution rights on the host running the sandbox," GitHub said in an advisory published on September 28, 2022.

The issue, tracked as CVE-2022-36067 and codenamed Sandbreak, carries a maximum severity rating of 10 on the CVSS vulnerability scoring system. It has been addressed in version 3.9.11 released on August 28, 2022.
vm2 is a popular Node library that's used to run untrusted code with allowlisted built-in modules. It's also one of the most widely downloaded software, accounting for nearly 3.5 million downloads per week.
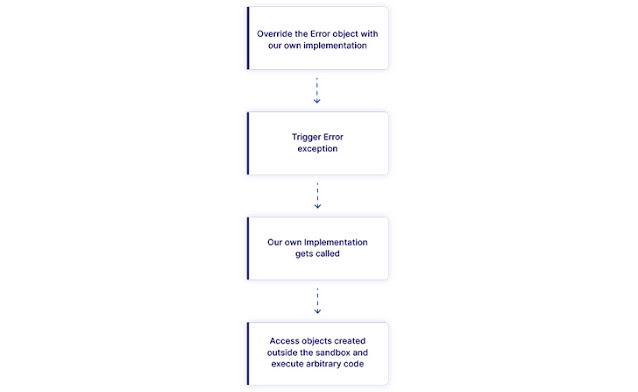
The shortcoming is rooted in the error mechanism in Node.js to escape the sandbox, according to application security firm Oxeye, which discovered the flaw.
This means that successful exploitation of CVE-2022-36067 could permit an attacker to bypass the vm2 sandbox environment and run shell commands on the system hosting the sandbox.
In light of the critical nature of the vulnerability, users are recommended to update to the latest version as soon as possible to mitigate possible threats.
"Sandboxes serve different purposes in modern applications, such as examining attached files in email servers, providing an additional security layer in web browsers, or isolating actively running applications in certain operating systems," Oxeye said.
"Given the nature of the use cases for sandboxes, it's clear that the vm2 vulnerability can have dire consequences for applications that use vm2 without patching."
Channels between sandbox and host
Like several previous bugs found in vm2, the new bug relies on the channels the sandbox uses to communicate with the host machine. In this case, the bug was caused by improper exception handling.
“The bug we found relies on a technique that is quite common in the VM bypass world, which is to find elements within the sandbox that can cooperate with elements outside of it,” the researchers said.
“This connection, when found, gives the attacker the opportunity to interact with the hosting process.”
This channel allows the attacker to run arbitrary code on the Node.js server, including invoking functions that run system commands.
The team aims to release a technical review of the bug with more details soon. The only way to prevent exploits is to upgrade to the newest version of vm2.
‘Meant to run untrusted code’
“We weren’t surprised by the fact that this library is used in production environments, mainly due to the fact that it has over 16 million downloads per month,” the researchers said. “We are in the process of responsible disclosure with several companies where we found this vulnerability in.”
In a separate advisory, RedHat has released a list of its services that are affected by the vm2 flaw.
This is not the first time that vm2 has patched a sandbox bypass, which only highlights the difficulties of securing sandbox environments.
“Sandboxes in general are meant to run untrusted code within an application. This means that you shouldn’t automatically assume that they are safe,” the researchers said.
“If the use of a sandbox is unavoidable, we recommend separating the logical, sensitive part of the application from the microservice that runs the sandbox code so if a threat actor successfully breaks out from the sandbox, the attack surface is limited to the isolated microservice.”